Storing secrets with AWS Secrets Manager
General
AWS allows a number of ways to hold the secrets needed to build applications in the cloud. Today, I'm going to focus on AWS Secrets Manager.

The AWS page about AWS Secrets Manager you can find here.
Inside this service we can both add credentials e.g. for databases, various API keys third party apps we use. In addition, it is possible to rotate keys at different time intervals, monitor access and much more.
Some cool features:
- Change secret in one place, all applications using it can use it immediately.
- Creation of new secrets (for supported services, e.g. RDS).
- Automatically rotate secrets (to supported services e.g. RDS).
- It's more secure (logged access).
Quickly about pricing: $0.40 per secret per month, and $0.05 for 10 000 requests. There is a calculator which will help to estimate costs.
Creating example API key
Let's create a new secret for the API Key. Navigate to the AWS Console, open the Secrets Manager service.
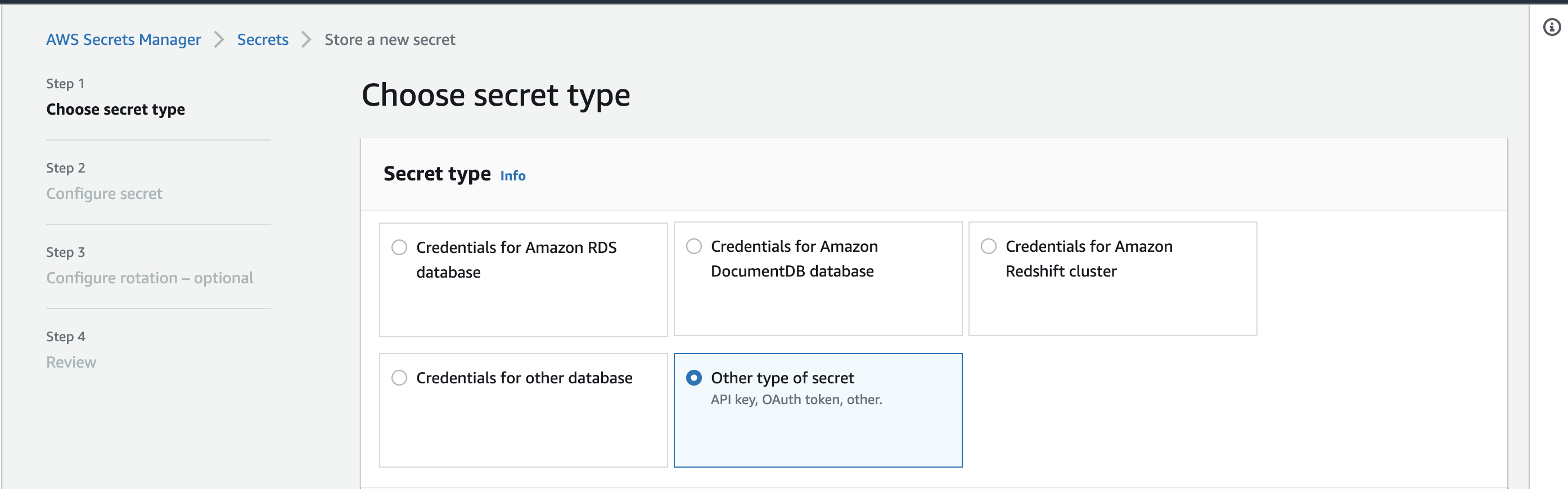
First you have to choose secret type, please do select Other type of secret option:
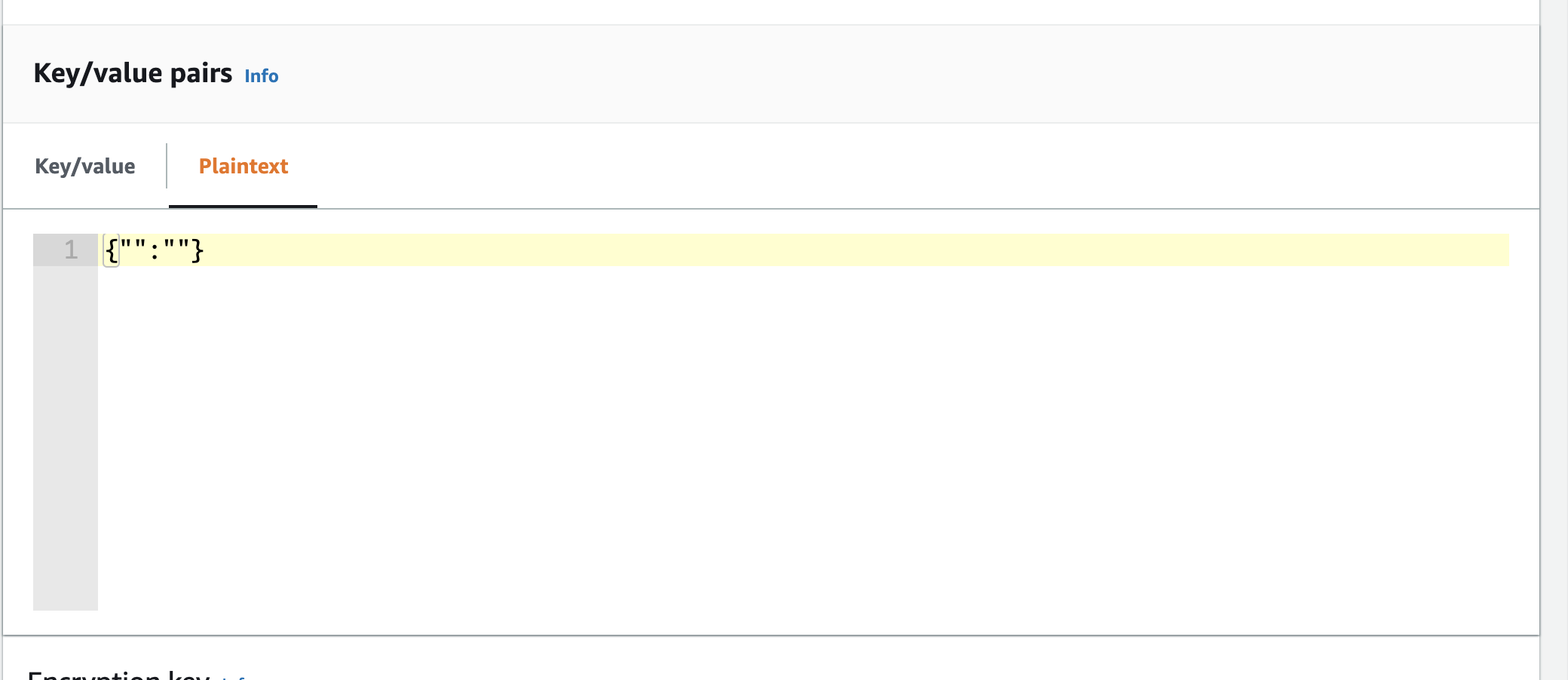
Navigate to Key/value pairs and select Plaintext
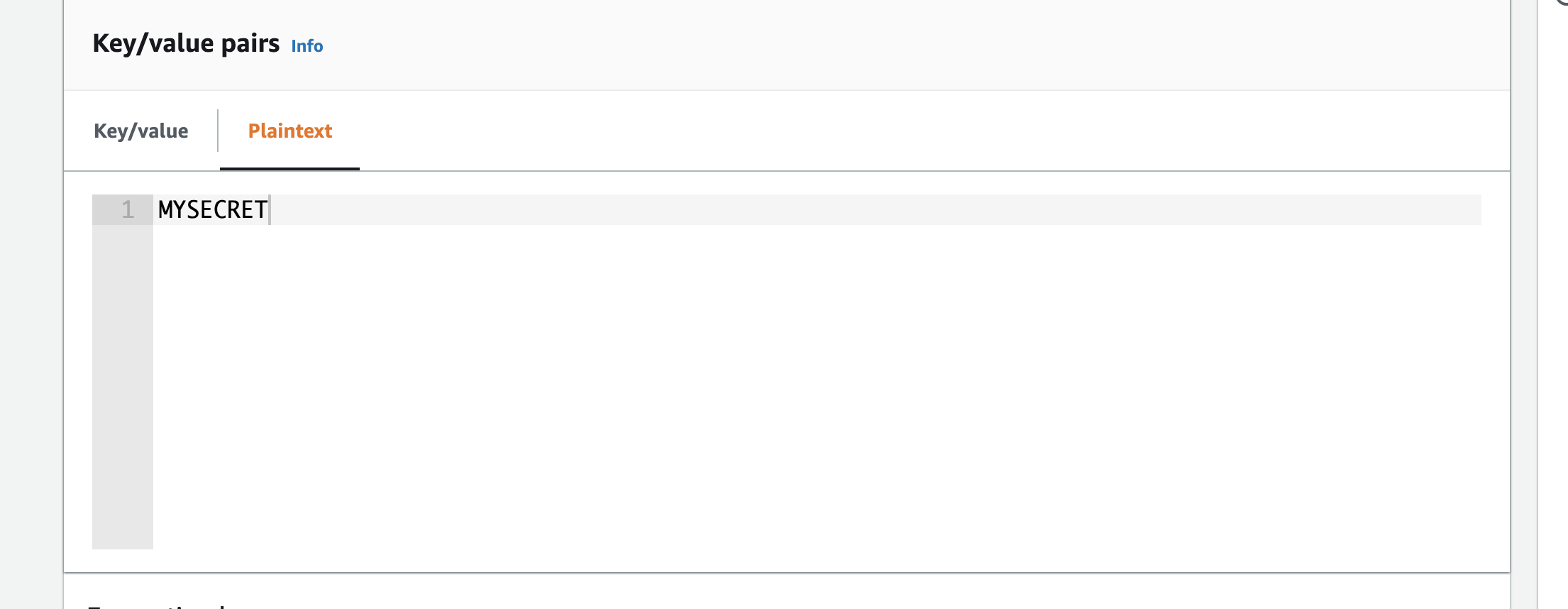
Clear the default value, and add your api key value without the quotes:
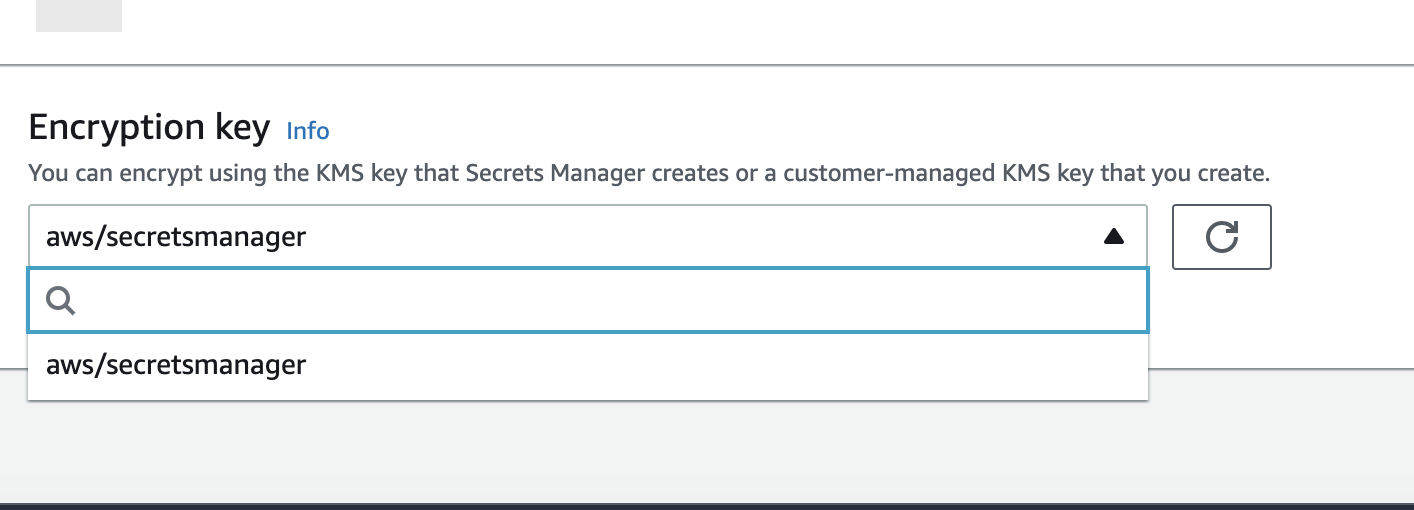
Select aws/secretsmanager as an encryption key. Hit next.
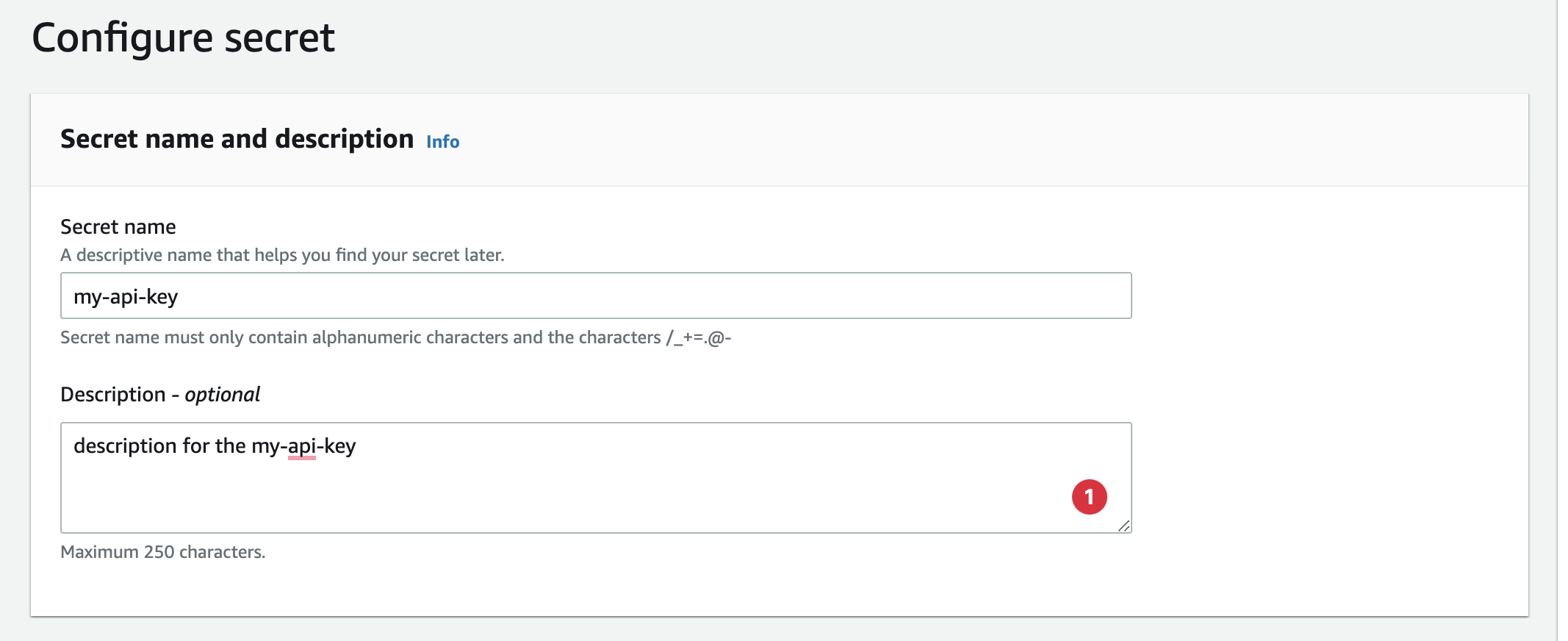
Add name and description:
If your need your replicate your secret to other regions, you can do it here:
In the next step, you can configure your automatic rotation if it's needed.
In the last step you can review your secret, and see how to access it via AWS SDK.
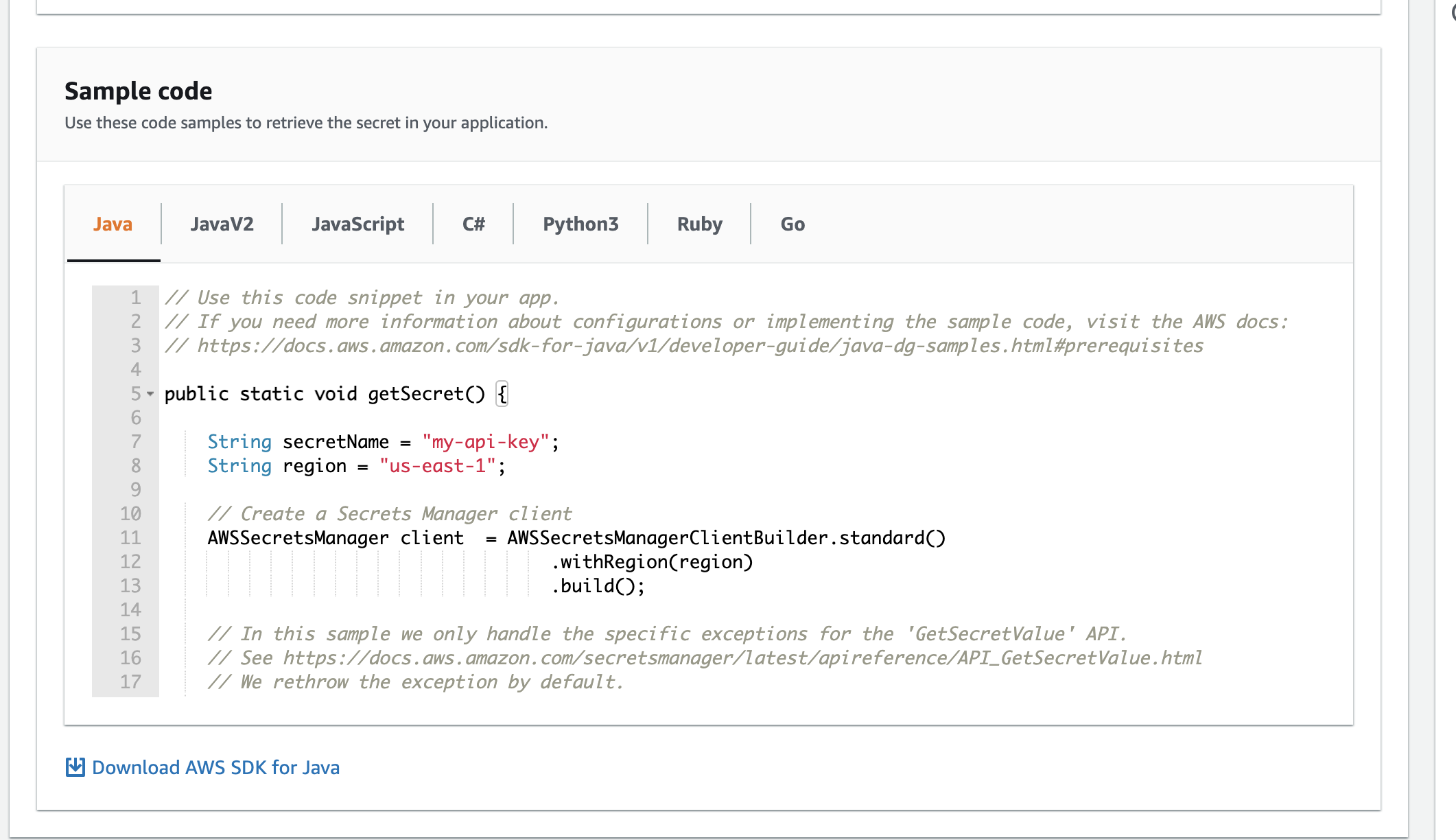
After submit, you can see green notification:
Easy, as that :) Now let's try to access newly created API key in our serverless.yml file:
See the Serverless Framework syntax.
For accessing API key from the NodeJS/TS check this code:
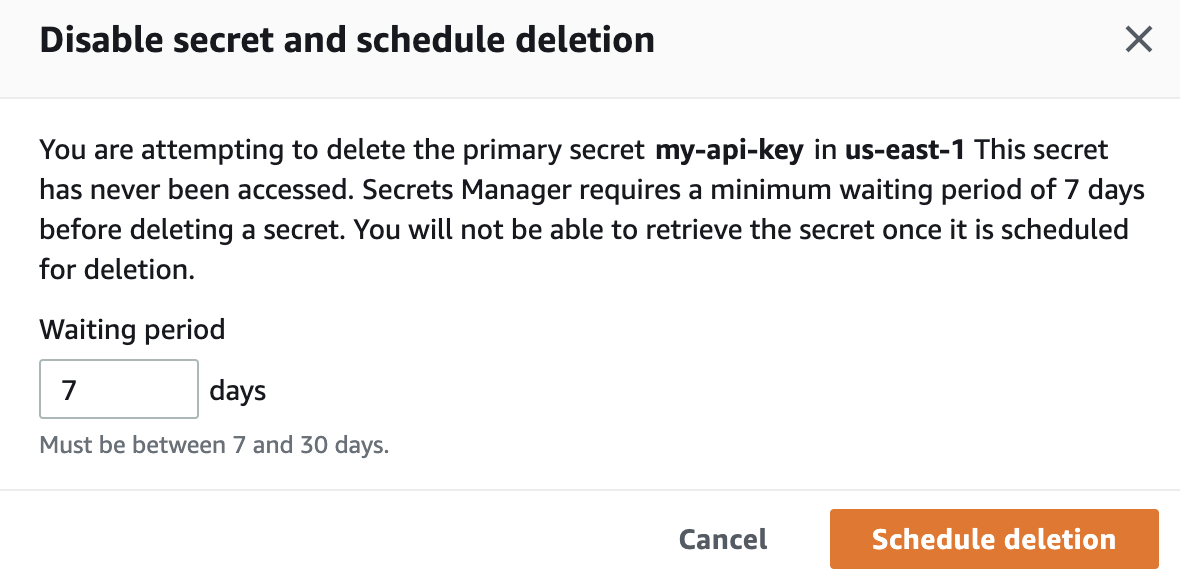
Deleting secret
Simply open the secret hit actions and click delete secret, you will the modal: